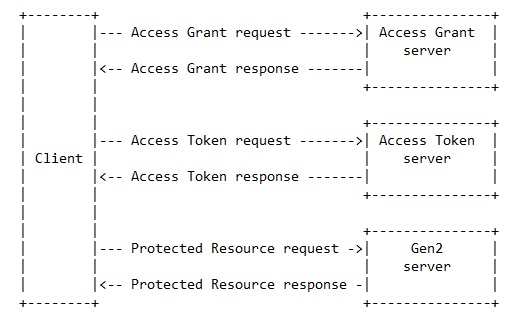
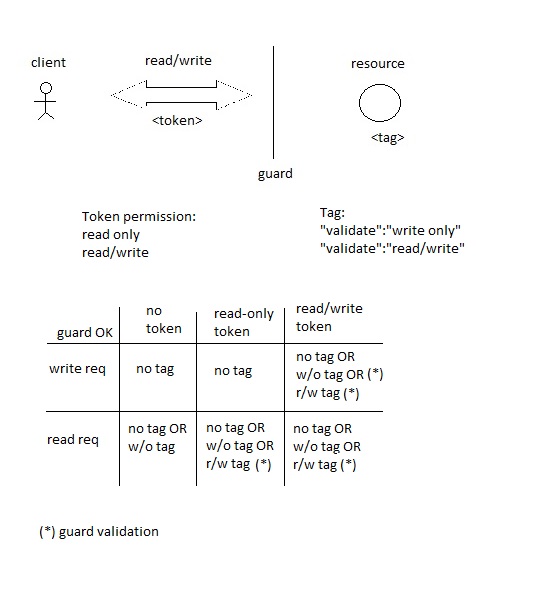
Data Model
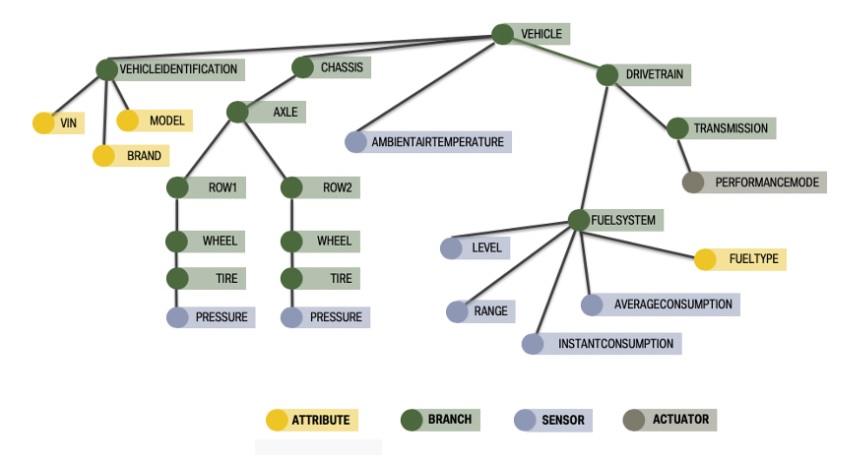
The service is intended for use with a tree-like logical taxonomy to represent the vehicle data. An illustrative example of such a tree structure is shown in Figure 1. While it is meant to support conforming taxonomies it was created principally with the Vehicle Signal Specification (VSS) in mind. For more details, see the VSS documentation.
Addressing
Addressing of elements is done using URIs as defined in [[RFC3986]].
scheme:authority/path?query
The scheme describes the protocol to use to reach the addressed element.
The authority describes where to reach the server holding and managing the data representation. Scheme and authority are defined within the protocol adaptation.
The path consists of the slash delimited node names of the nodes traversed from the tree root to the tree leaf representing the data point. E. g. the path expression from traversing the nodes Vehicle, Car, Engine, RPM would be "Vehicle/Car/Engine/RPM". The VSS data model uses a dot as delimiter, the implementaion of this specification is expected to handle the necessary translation.
The query contains further information related to the request, see .
Service Discovery
The purpose of the data model is to provide a client with a description of the data that enables the client to make a request for desired vehicle data,
and interpret the response. In order to obtain that description, the client MAY request that the server returns the VSS tree content,
i. e. the metadata describing the accessible vehicle data. The client is able to request metadata from any point in the signal tree,
such that only the metadata for the nodes within the given branch of the tree is returned. For example,
only metadata for the chassis branch of the VSS tree is returned when the chassis path is specified.
If the path is set to the VSS root, the response contains the metadata for the entire tree. If the server is able to satisfy the request it SHALL return a Response message.
If an error occurs the server SHALL return an ErrorResponse message.
Some parts of the VSS tree may not be accessible to the Client due to restrictions defined in the .
A service discovery request has the format of a read, where the path is appended with a query component,
see for the details.
The key data components of these messagess are defined below:
- Request message parameters:
- Path: The address to one or more nodes in the VSS tree, followed by the query component specifying the service discovery.
- Response message parameters:
- Metadata: The content of the VSS tree where the root is specified by the path.
- Timestamp: A timestamp associated with the request.
- ErrorResponse message parameters:
- Error: Information describing the error reason.
- Timestamp: A timestamp associated with the failed request.